Subscribe to our news letter to get the latest on Google Cloud Platform and more!
Best Practices for Cost Optimization in Google Cloud: A GCP Guide 2025
As organizations increasingly migrate to cloud platforms, understanding the intricacies of cost…

As organizations increasingly migrate to cloud platforms, understanding the intricacies of cost…
In the evolving landscape of cloud computing, organizations are increasingly turning to…
Introduction: The Journey from Keys to Federation In the early days of…
Subscribe to our news letter to get the latest on Google Cloud Platform and more!

In the early days of cloud authentication, service account keys were the go-to solution for applications and users needing access to Google Cloud resources. These keys were tangible—JSON files containing credentials that could be easily stored, managed, and shared. But with this simplicity came significant responsibility.
For security-conscious teams, storing these keys securely became paramount. Enter vault solutions. Organizations set up sophisticated vault systems to encrypt and manage these keys. Yet, this came with its own challenges. Setting up a vault involved intricate configurations, ensuring high availability, and managing permissions. Every interaction—whether an application fetching a key or a user accessing the vault—added layers of complexity and potential points of failure.
The process became a cycle: generate the key, store it in the vault, retrieve it securely, and use it to authenticate. For a simple task like accessing a cloud resource, the overhead was immense.
Then came Workload Identity Federation in Google Cloud, a paradigm shift that replaced this cumbersome process with elegance and efficiency. With Workload Identity Federation, service account impersonation became the cornerstone of cloud authentication. Instead of relying on long-lived keys, applications could now authenticate using short-lived tokens derived from external identity providers.
The vault setup? No longer necessary. The risk of key compromise? Drastically reduced. By directly integrating with trusted identity providers like OIDC, organizations could securely authenticate workloads and users without ever touching a service account key.
This innovation not only simplified authentication but also improved security posture, making it easier for developers and administrators to focus on building and scaling applications without worrying about key management.
At the heart of Workload Identity Federation lies the Workload Identity Pool—a powerful construct that bridges external identities with Google Cloud. In essence, a workload identity pool allows you to manage external identities, enabling workloads running outside Google Cloud to authenticate seamlessly.
Before diving into the technical details, let’s simplify things with an analogy. Sometimes, abstract concepts like workload identity pools are easier to grasp when compared to everyday experiences. So, let’s think about how access works in a familiar setting—like a hotel.
Just like hotels don’t rely on permanent keys—avoiding the risk of lost or stolen keys—workload identity pools eliminate the need for long-lived service account keys. This ensures secure, temporary access, making cloud resource management safer and more efficient.
Consider a typical organization with multiple environments: development, staging, and production. Each environment may run on different platforms—Kubernetes clusters, on-premise servers, or even other cloud providers like AWS or Azure. Managing service account keys across these environments can quickly spiral into a logistical and security nightmare.
With workload identity pools, however, you can:
A key recommendation in designing your identity strategy is to create a separate workload identity pool for each environment. Here’s why:
Imagine you’re staying at a hotel. When you arrive at the front desk, they don’t hand out permanent keys to guests. Instead, they verify your identity and check your reservation. Once everything is confirmed, they issue you a key card—a temporary pass that grants access to your specific room for the duration of your stay.
Here’s how this maps to Workload Identity Pools:
When your stay is over, the key card stops working. Similarly, the credentials issued by workload identity pools are temporary, reducing the risk of misuse or exposure.
While Workload Identity Pools serve as the gatekeepers for external identities, Workload Identity Providers define the actual pathways between Google Cloud and your external Identity Providers (IdPs). A workload identity provider describes the relationship between Google Cloud and the IdP, specifying how external identities can authenticate and obtain access.
Google Cloud supports a wide range of IdPs, allowing flexibility in integrating various environments and platforms. Here are some examples:
Workload Identity Federation is built on the OAuth 2.0 token exchange specification, ensuring a secure and standard process for obtaining credentials.
Here’s the flow:
This system eliminates the need for long-lived credentials, such as service account keys, reducing security risks. It also simplifies the integration of external systems with Google Cloud, as workloads can use their existing identities and authentication mechanisms without requiring direct user intervention.
Let’s revisit our hotel analogy to better understand Workload Identity Providers.
In a hotel, the front desk (Workload Identity Pool) doesn’t just issue key cards to anyone. It needs to know who you areand where you’re coming from before granting access. This is where Workload Identity Providers come in—they act as the trusted verifiers for the hotel, confirming your identity before the front desk gives you access to your room.
In this scenario, the hotel might accept multiple forms of ID based on who you are and where you’re coming from:
Once your identity is verified by the trusted verifier (Workload Identity Provider), the front desk issues your key card(federated token) to access your specific room (Google Cloud resources).
In technical terms, this process follows the OAuth 2.0 token exchange:
By leveraging workload identity providers, the hotel (Google Cloud) can work with a variety of trusted verifiers, ensuring flexible and secure access for guests (workloads) coming from multiple sources. This eliminates the need for carrying permanent keys (long-lived credentials) and makes access more secure and manageable.
In this demo, we’ll walk through the steps to set up Workload Identity Federation. This involves creating a service account with the required permissions and configuring a Workload Identity Pool to authenticate external workloads.
First, we’ll create a service account that external workloads will impersonate when accessing Google Cloud resources.
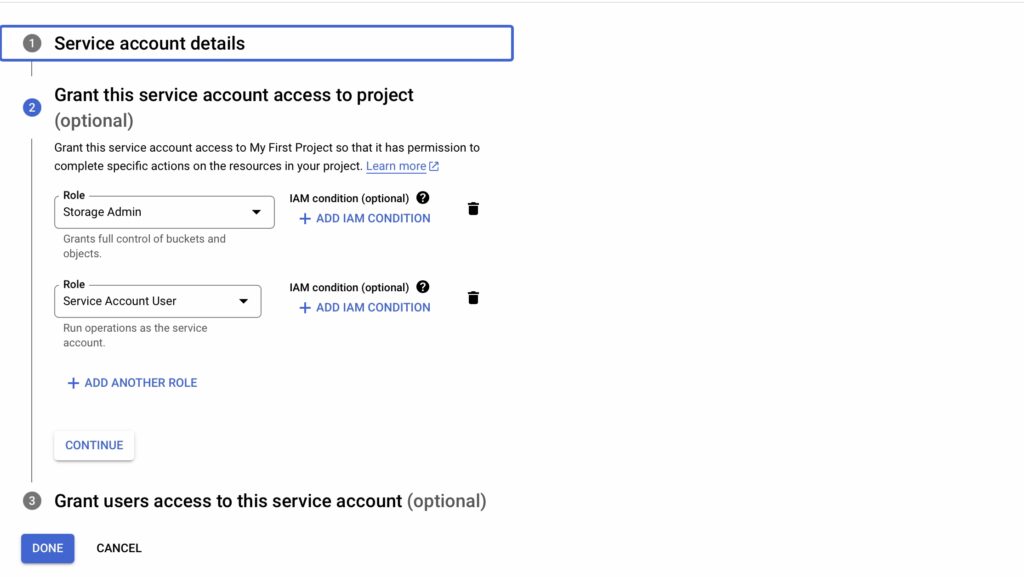
Next, we’ll create a Workload Identity Pool to authenticate identities from external providers.
external-id-pool).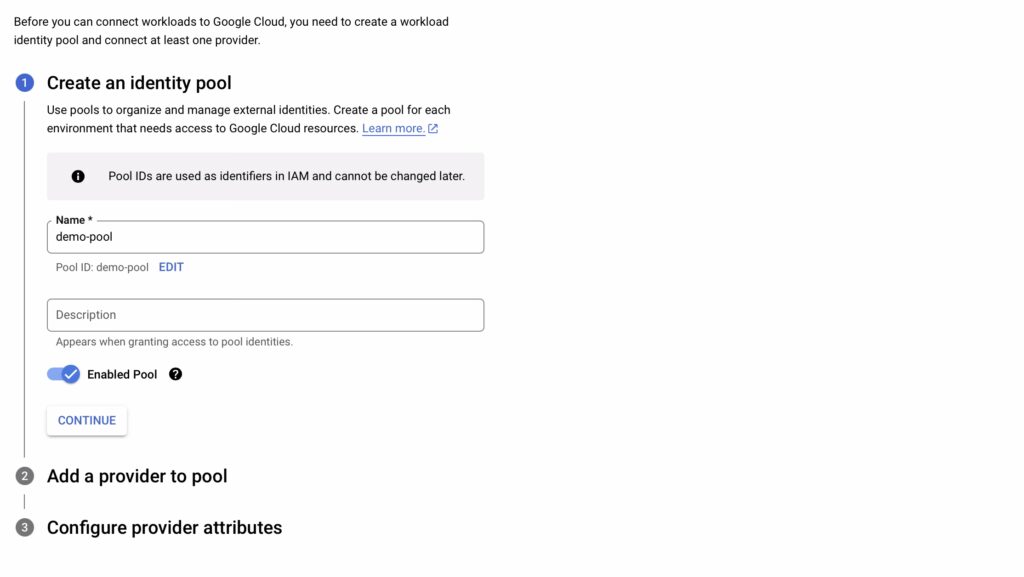
A Workload Identity Pool needs a provider to verify external identities.
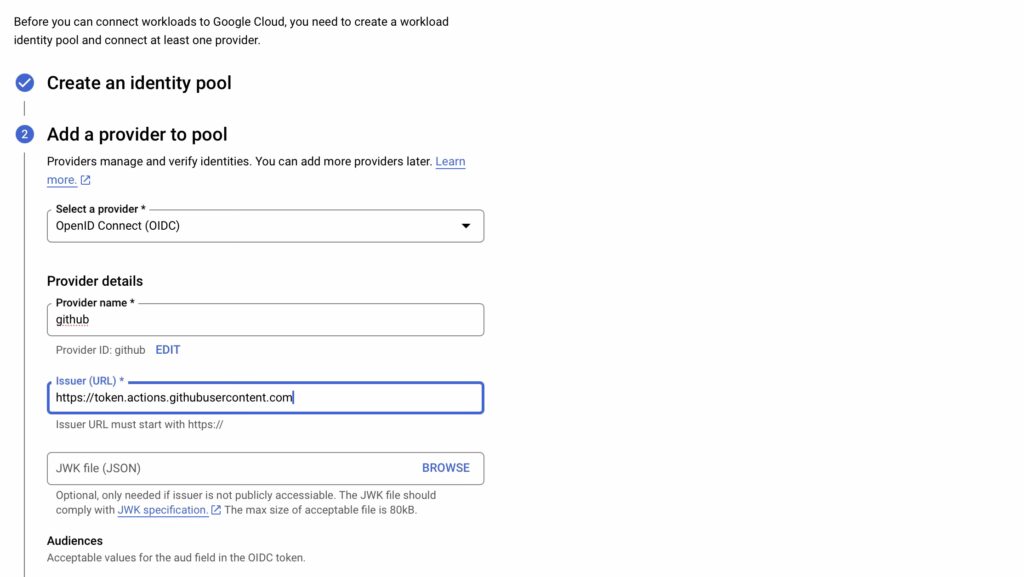
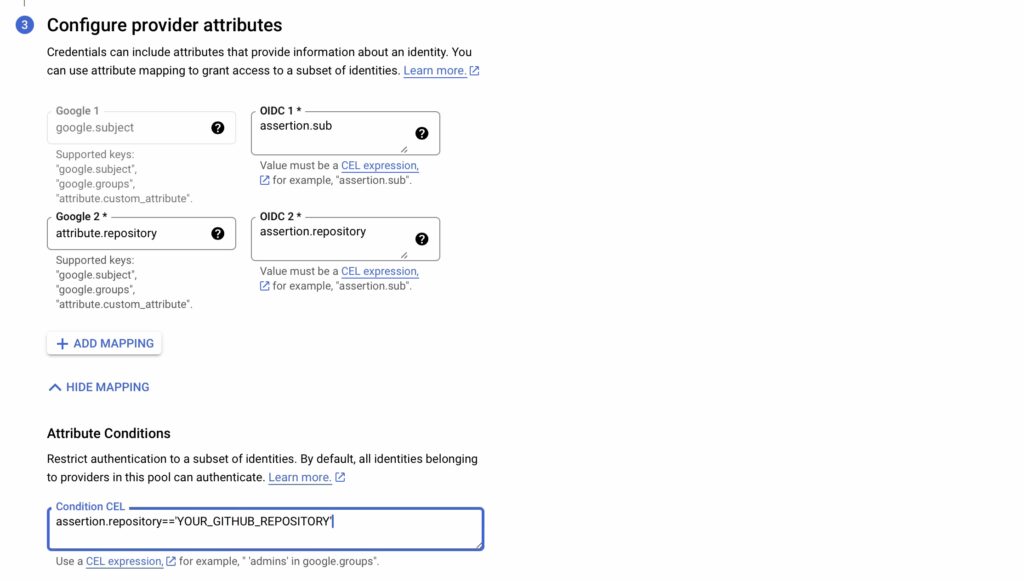
Finally, allow identities in the pool to impersonate the service account.
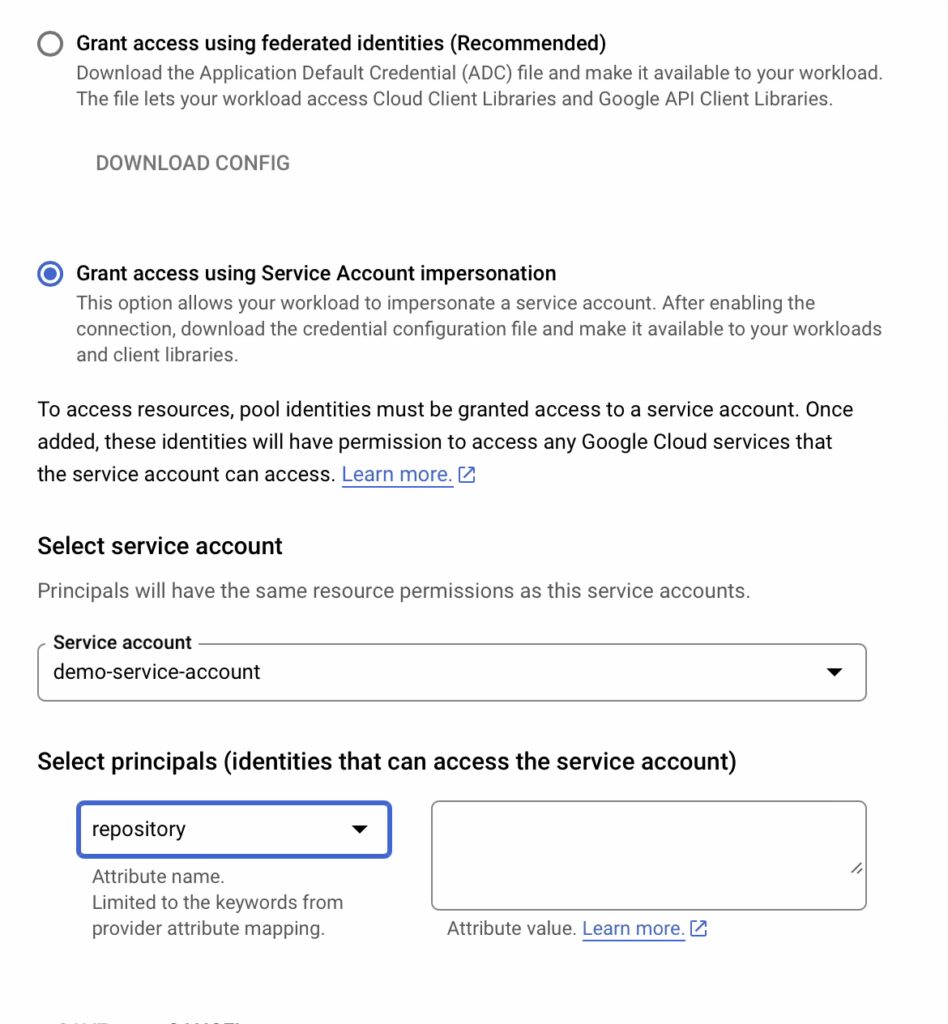
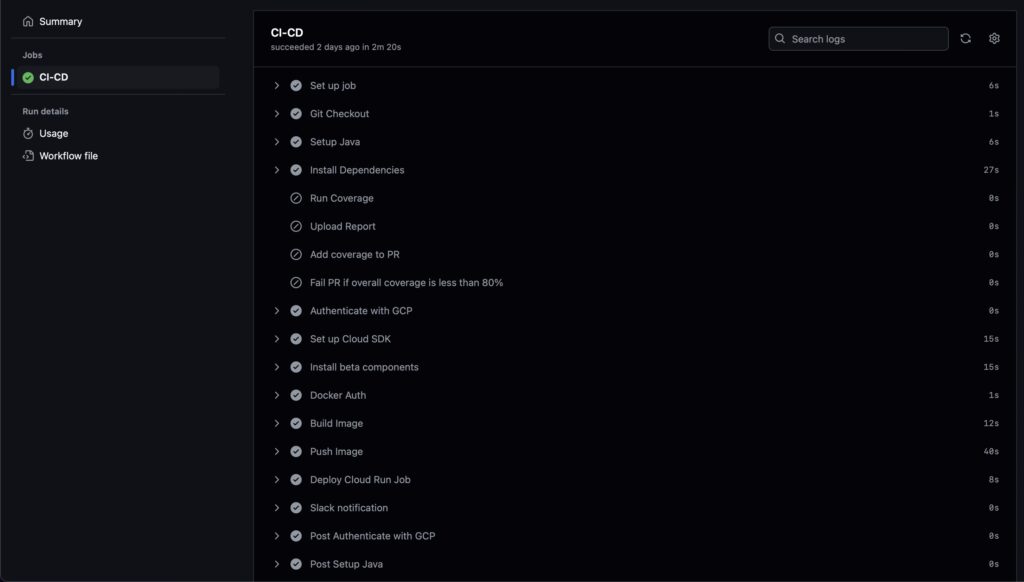
Now that we have all the initial setup ready, Lets see the workflow in action. I had already explained about the Github action in my previous blog post
Workload Identity Federation in GCP represents a transformative step forward in cloud authentication, replacing long-lived keys with secure, temporary tokens derived from trusted identity providers. By integrating this feature into your workflows, you not only enhance security but also streamline access management across diverse environments.
From eliminating the overhead of key management to enabling seamless authentication for platforms like GitHub, Workload Identity Federation empowers organizations to focus on innovation rather than infrastructure.
Whether you’re scaling your CI/CD pipelines, connecting external workloads, or ensuring compliance, this approach aligns with modern best practices for cloud-native security.
By adopting Workload Identity Federation, you’re future-proofing your cloud strategy—embracing a model that prioritizes security, simplicity, and scalability.